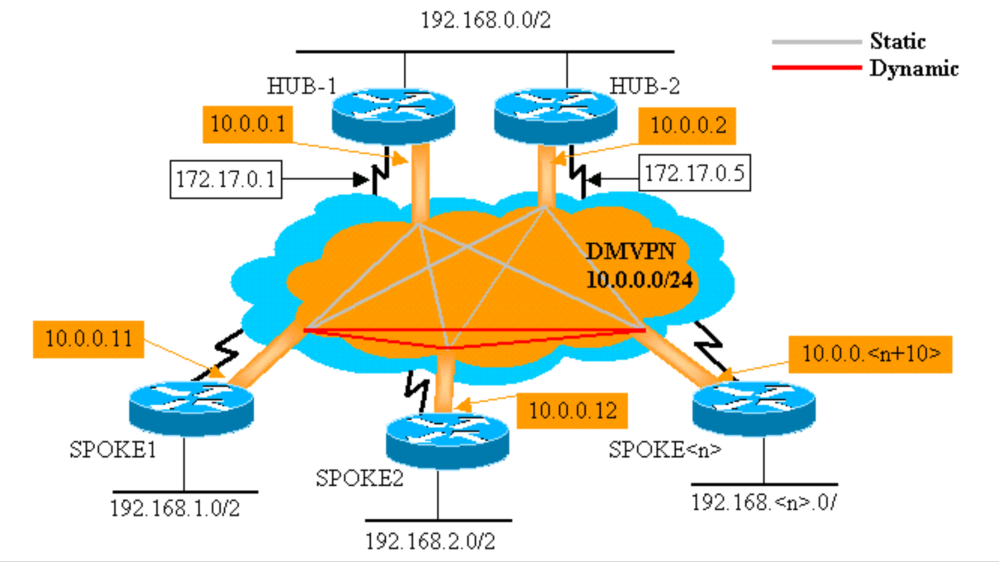
Lab: Dual Hub - Single Cloud DMVPN
Here's a lab I'm currently working on:
Dual Hub - Single Cloud DMVPN.
I recently jumped into DMVPN and holy smokes, I wish I found it sooner. In general, anything dynamic in networking is a good thing. Its usually less painful to configure than a static method and it allows the algorithms to perform their magic. Sure you could use static routes everywhere, but advertising a network out of a dynamic protocol makes so much more sense.
So why am I so excited about DMVPN? Last year I was tasked with a project that required building 150 GRE IPSec tunnels. This required an enormous amount of time and effort. After creating a god awful long script to make the changes, I then had the pleasure of dealing with change management; repeatedly. Don't get me wrong, I understand the need for change management and appreciate its value in minimizing impact and coordinating a lot of moving parts. But add the administrative burden of it all to having to perform the work at odd hours (translation - I should be asleep) and its a bit unpleasant.
On more than one occasion I had to go back and fix head-end router configs related to the static tunnels, some of which weren't coming up. Mismatched crypto keys, policies, syntax errors, and botched addressing were a few of my missteps. After figuring out my mistakes and building scripts to fix them, I had to start from scratch with change management. Oye vey.
The beauty of DMVPN is the ability to preconfigure the head-end routers, which never have to be touched again. You can dynamically bring up as many tunnels as you'd like, from the edge, without touching routers that require the inherent red tape of change management. So the aforementioned 150 static tunnels I suffered through could have been created during normal business hours, with no CRQ required. Needless to say that moving forward I will do my best to stick with the design concept of DMVPN. At a minimum, its just a more efficient use of time. Live and learn.
Red tape aside, DMVPN is lean and mean. Once I got the concepts down and got my first DMVPN lab working, confusion became excitement. Multipoint GRE enables a tunnel to have multiple destinations, where traditional GRE is strictly point to point. This enables a hub router to tunnel up with multiple spokes, without having to statically define each tunnel in the hub. This greatly reduces the administrative burden on the hub. Remember those 150 tunnels from earlier in this post? Yeah, that was A LOT of hub configuration; booooooooo.
The other special sauce of DMVPN is NHRP, or next hop resolution protocol. mGRE creates an NBMA network. NHRP performs a few key functions in this NBMA environment, namely registration and resolution.
First, it allows clients (spokes) to dynamically register with servers (hub). This functionality allows the clients to join the NBMA network without having to make config changes in the hub. This dynamic registration is especially useful when the client has a dynamically assigned outside IP address, which is subject to change when its lease expires. A client with a dynamic outside address would make preconfiguration on the hub impossible, as the connectivity would tear down when the spoke's outside address changes.
The second key function of NHRP is resolution. Namely, it allows one spoke to dynamically discover (resolve) the logical VPN IP to physical NBMA IP mapping of another spoke on the same NBMA network. This allows spokes to communicate directly with each other, rather than hair-pinning through the hub.
The reduction in administrative burden of DMVPN over statically defined tunnels is another huge benefit of this suite of technologies. I could have shaved endless hours off of last year's project if that environment supported DMVPN. "Zero-touch configuration" sounds like a dream, compared to the countless hours I spent last year building (and fixing) 150 GRE IPSec tunnels.
Here's what my physical DMVPN lab looks like:
Here's what it looks like logically:
And here's the link to Cisco's white paper, which I'm following for this lab:
In summary, if you're building tunnels for security go with DMVPN. Unless you want to torture the new guy. Then make them build classic GRE IPSec tunnels.
Thanks for stopping by,
Andy